Overview
The VPS Firewall feature in the Virtualizor panel provides an advanced layer of security for your Virtual Private Server (VPS). It allows you to create and manage firewall rules/plans that control the traffic flowing in and out of your VPS, ensuring that your server is protected from unauthorized access and potential threats. It will work for VPS level firewall.
The
VPS Firewall in the Virtualizor panel is a powerful tool that helps you
safeguard your vps server by controlling network traffic. By setting up
customized firewall rules, you can prevent unauthorized access and
protect your VPS from potential threats, ensuring a secure and stable
environment for your applications and data.
Admin can also create a vps firewall plans for everyone from admin panel.
You can increase firewall_rule_limit in /usr/local/virtualizor/universal.php
VPS Firewall Config
To Apply the firewall Config Rules by VPS Plan, Users and VPS. To navigate this page you can go VPS Firewall --> VPS Firewall Config.
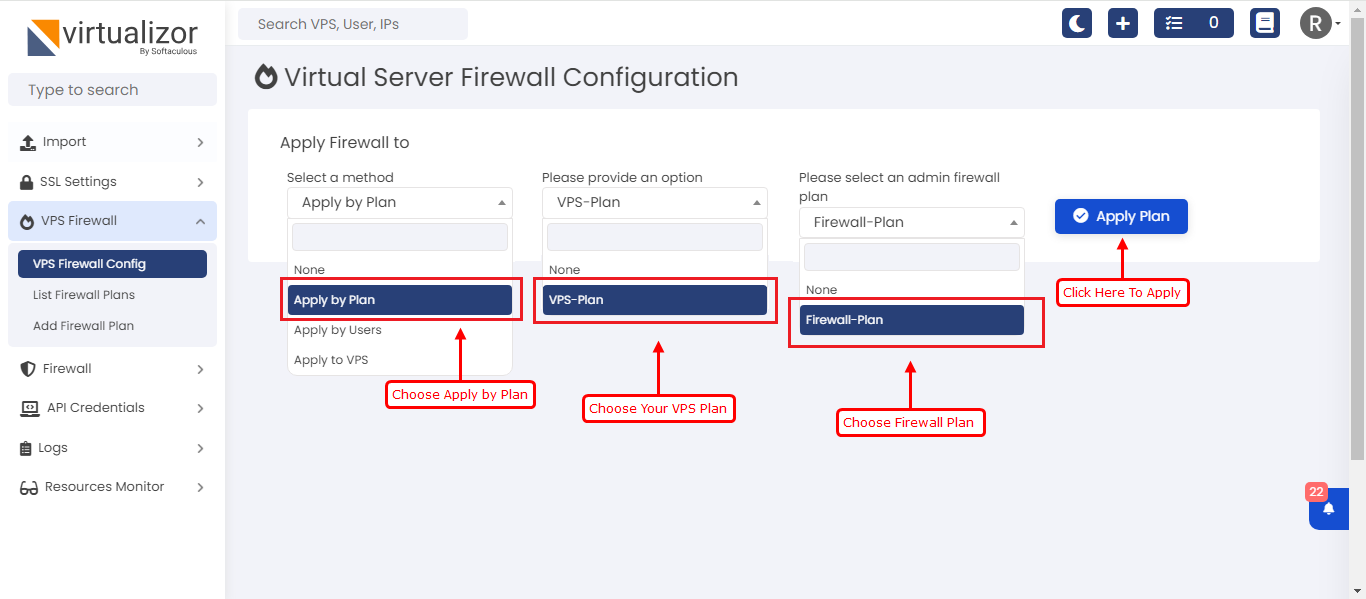
Apply By Plan
To apply the firewall rules to the vpses that are using same vps plans you can go with below screenshot steps.
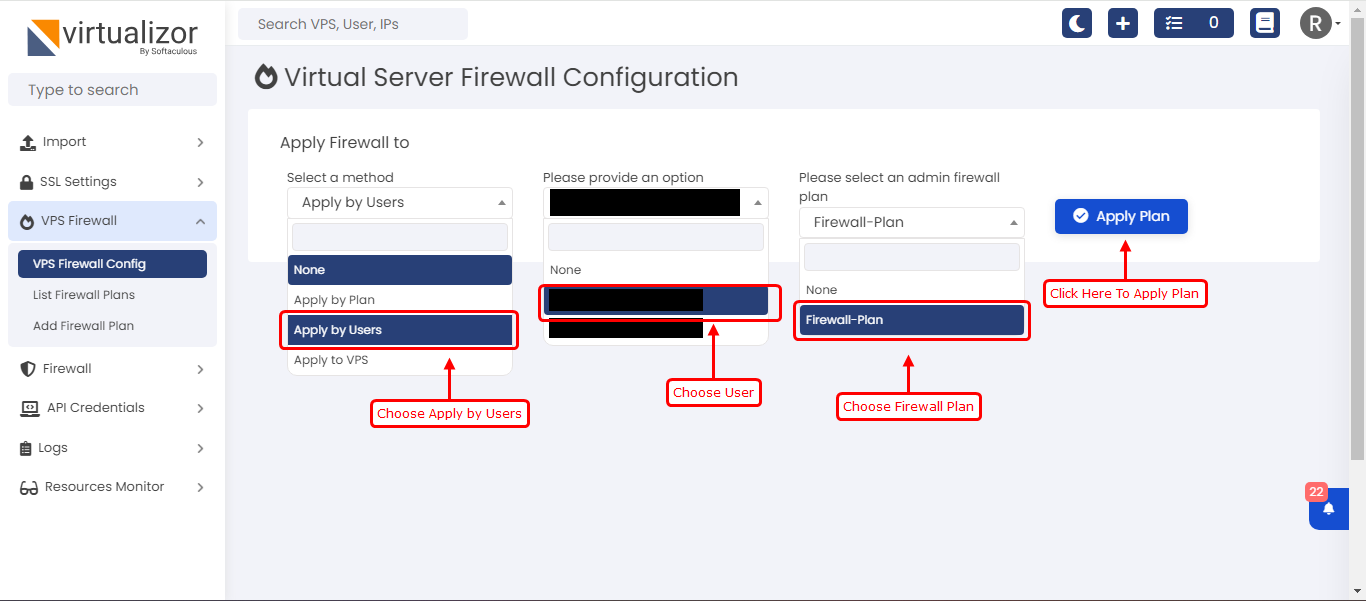
Apply By Users
To apply the firewall rules to the users vpses you can go with below screenshot steps.
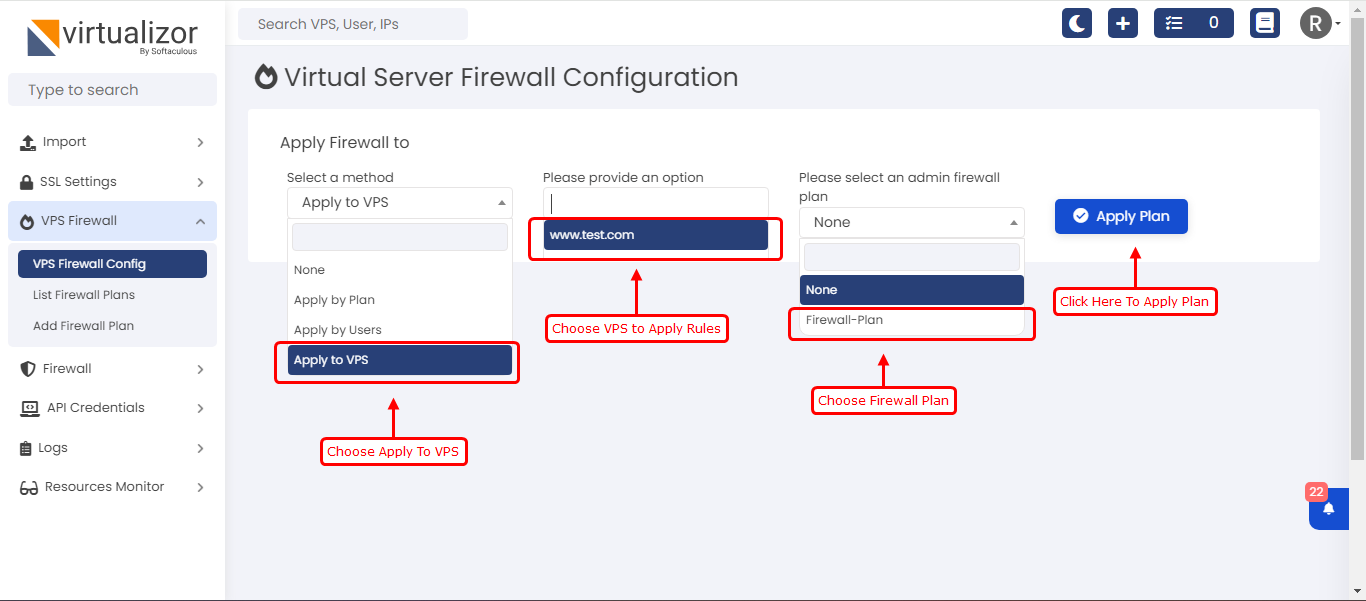
Apply To VPS
To apply the firewall rules to the vps you can go with below screenshot steps.
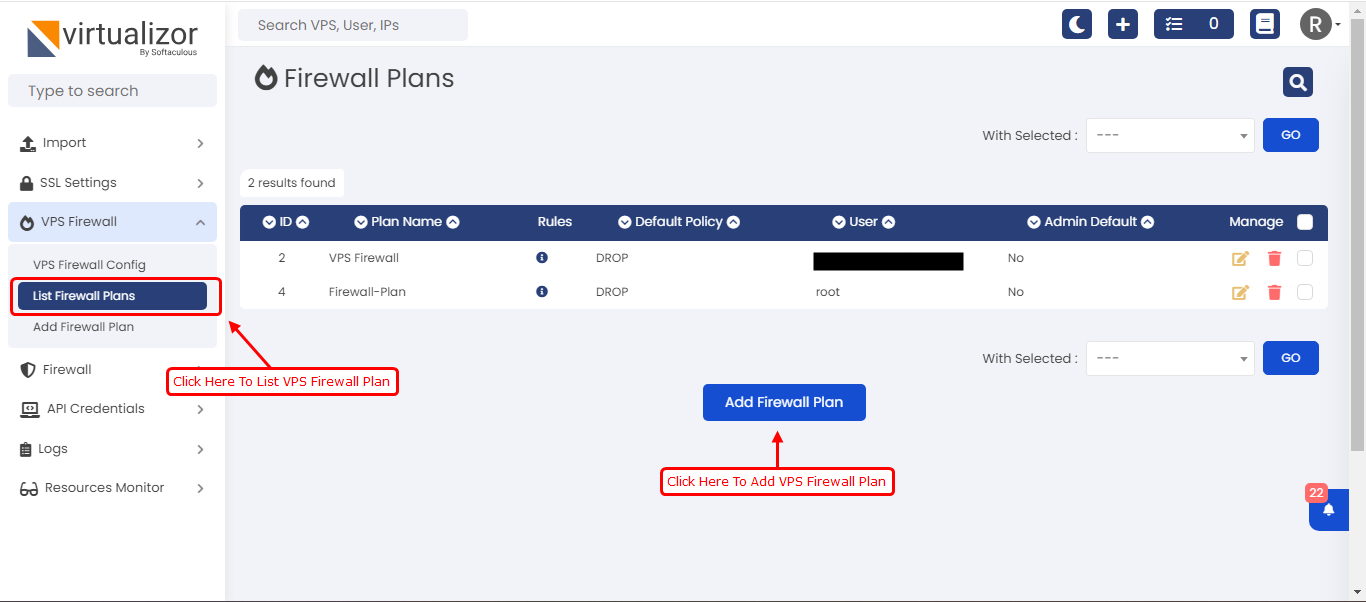
List Firewall Plans
To list the vps firewall plans you can navigate to VPS Firewall --> List Firewall Plans. All firewall plans created by Admin and Enduser(Cloud Users) will list here.
Add Firewall Plan
To add/create firewall plans you can navigate on VPS Firewall --> Add Firewall Plan.
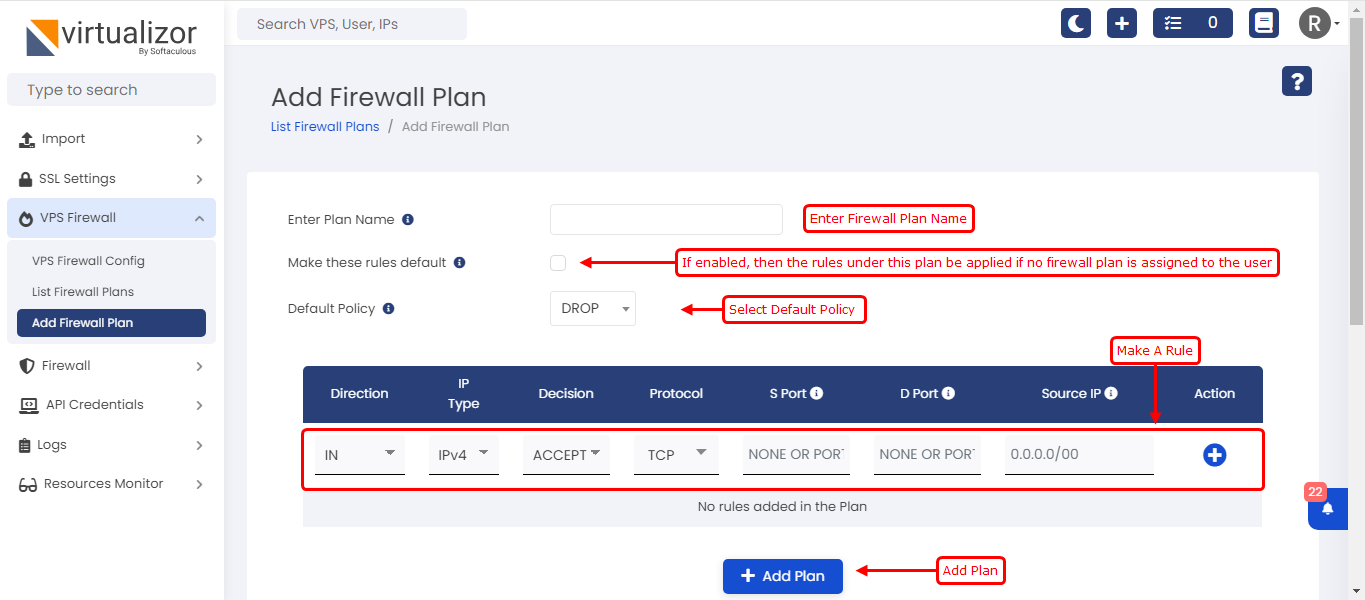
Terminology
Example :
To allow all outgoing connections for TCP.
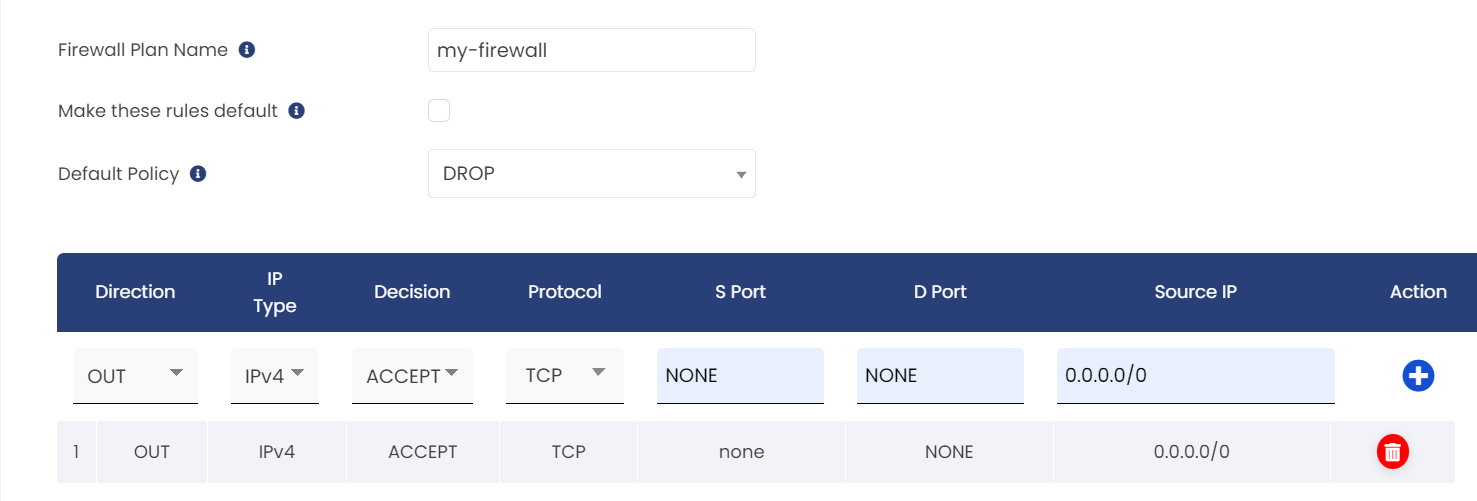
Explanation:
1. Default Policy: Drop All Connections
* This means that all incoming connections are blocked by default.
2. Allow outgoing connections (This rule should be clubbed with the other following examples, viz allowing SSH connections) :
*Direction: OUT (outgoing traffic)
*IP Type: IPV4
*Decision: ACCEPT (allow the connection)
*Protocol: TCP
*SPort (Source Port): None (not specified)
*DPort (Destination Port) : None (not specified)
*Source IP: 0.0.0.0/0 (any IP address can initiate the connection)
This will allow all outgoing connections from within VPS.
To allow yum install in specific VPS.
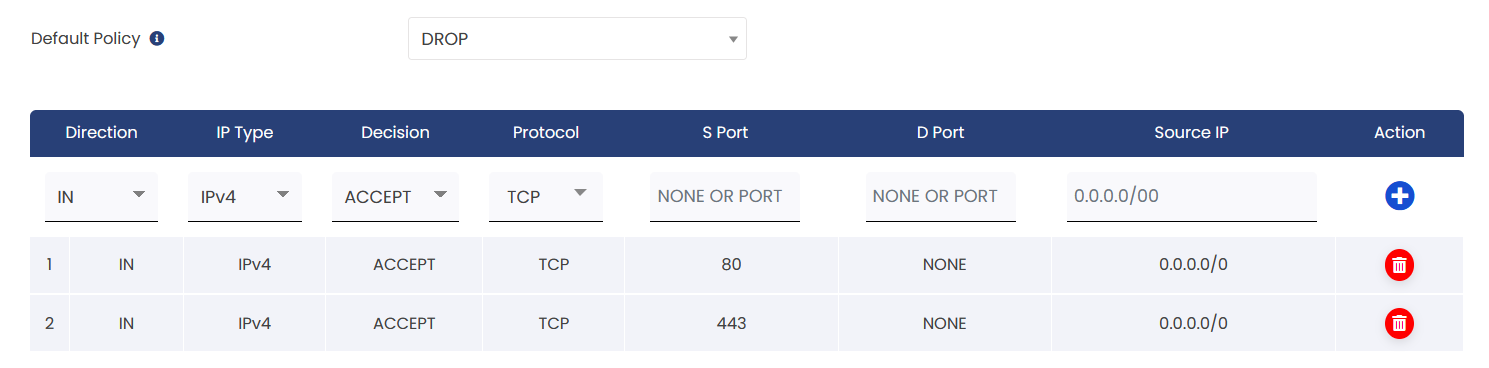
Explanation:
1. Default Policy: Drop All Connections
* This means that all incoming connections are blocked by default.
2. Exception for package installation :
*Direction: IN (incoming traffic)
*IP Type: IPV4
*Decision: ACCEPT (allow the connection)
*Protocol: TCP
*SPort (Source Port): 80 and 443 (the port used for package installation)
*DPort (Destination Port) : None (not specified)
*Source IP: 0.0.0.0/0 (any IP address can initiate the connection)
This will block all connection and only allow incoming traffic for port 80 and 443 from VPS .
To allow specific IP for SSH
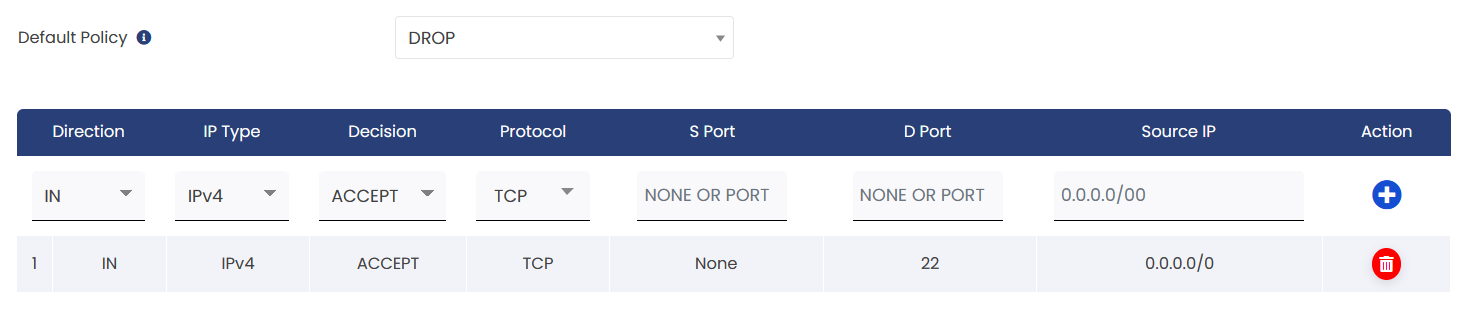
Explanation:
1. Default Policy: Drop All Connections
* This means that all incoming connections are blocked by default.
2. Exception for SSH Traffic:
*Direction: IN (incoming traffic)
*IP Type: IPV4
*Decision: ACCEPT (allow the connection)
*Protocol: TCP
*SPort (Source Port): None (not specified)
*DPort (Destination Port) : 22 (the port used for SSH)
*Source IP: 0.0.0.0/0 (all IP address can initiate the connection)
This will block all connections and allow only SSH access for everyone; if a specific IP address is mentioned, only that address will be granted access.
To Enable Ping from VPS
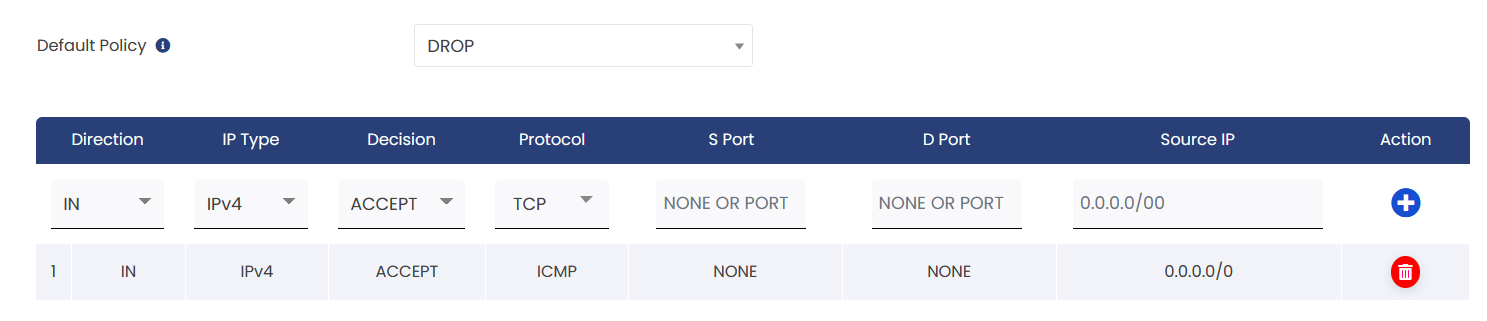
Explanation:
1. Default Policy: Drop All Connections
* This means that all incoming connections are blocked by default.
2. Exception for ICMP Protocol Traffic:
*Direction: IN (incoming traffic)
*IP Type: IPV4
*Decision: ACCEPT (allow the connection)
*Protocol: ICMP
*SPort (Source Port): None (not specified)
*DPort (Destination Port) : None (not specified)
*Source IP: 0.0.0.0/0 (to allow for all ip address)
This will allow to ping from VPS. to all, if a specific IP address is mentioned, only that address will be allowed to ping from vps.
To allow name resolution from VPS
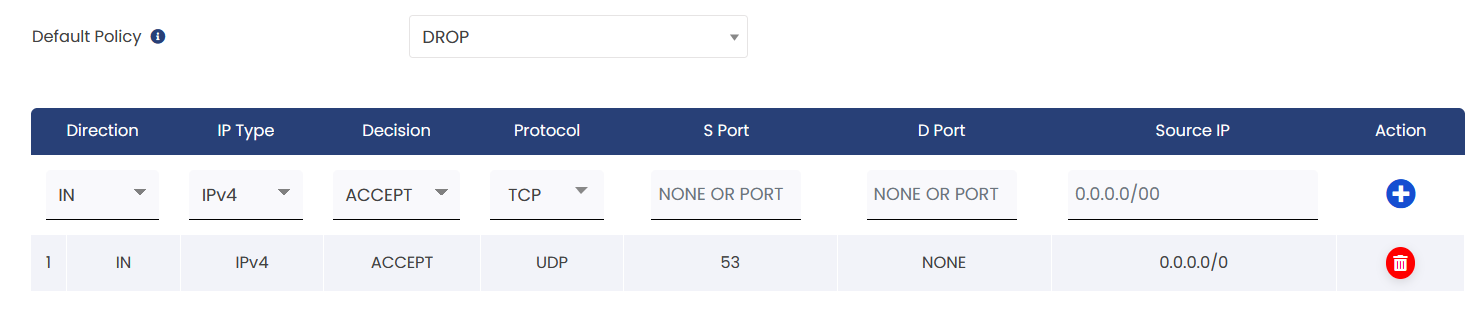
Explanation:
1. Default Policy: Drop All Connections
* This means that all incoming connections are blocked by default.
2. Exception to allow DNS (Domain Name System) services:
*Direction: IN (incoming traffic)
*IP Type: IPV4
*Decision: ACCEPT (allow the connection)
*Protocol: UDP
*SPort (Source Port): 53 (the port used for DNS)
*DPort (Destination Port) : None (not specified)
*Source IP: 0.0.0.0/0 (To allow all IP address)
To block SMTP port for VPS
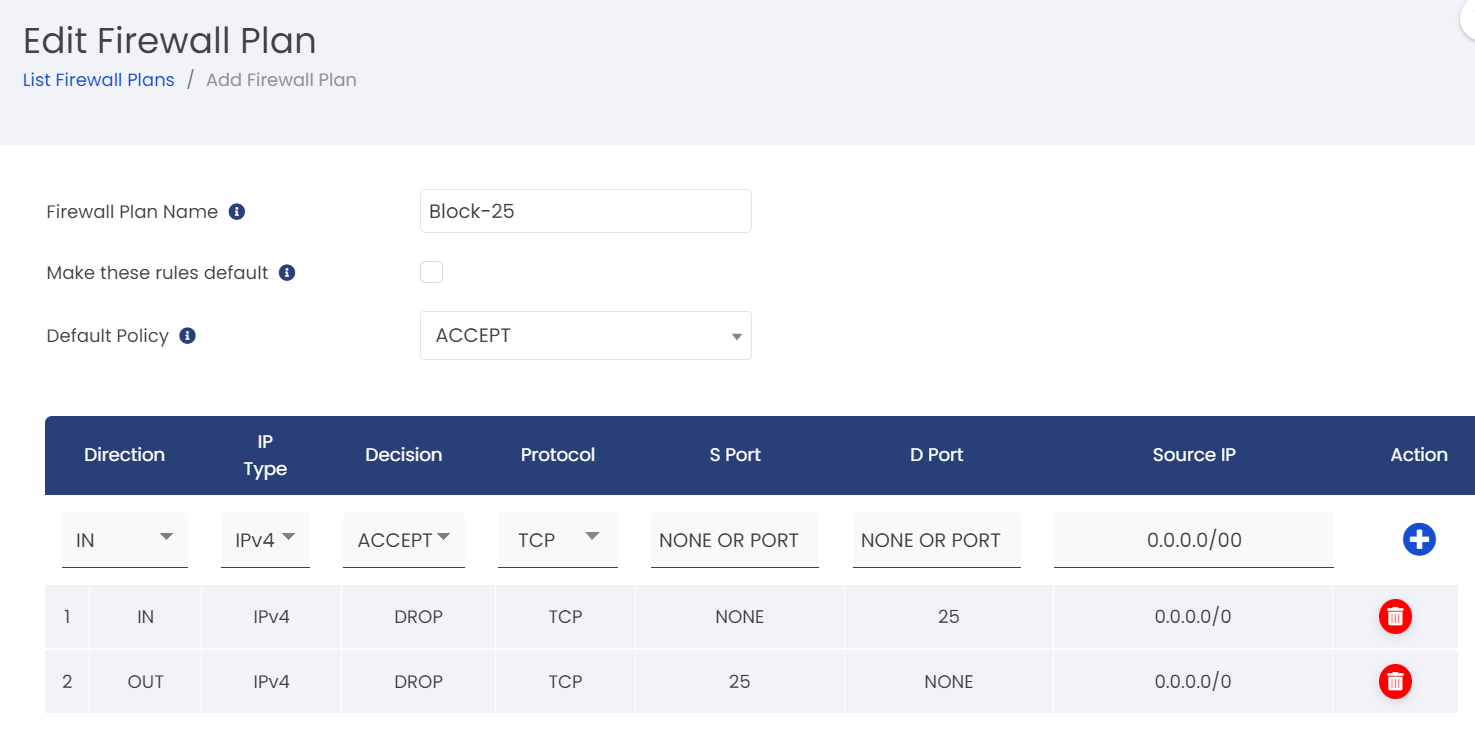
Explanation:
1. Default Policy: ACCEPT All Connections
* This means that all incoming connections are ACCEPT by default.
2. Exception to Block Email services :
*Direction: IN (Incoming traffic)
*IP Type: IPV4
*Decision: DROP (Drop the connection)
*Protocol: TCP
*SPort (Source Port): None (not specified)
*DPort (Destination Port) : 25 (Port used for Email)
*Source IP: 0.0.0.0/0 (To allow all IP address)
*Direction: OUT (Outgoing traffic)
*IP Type: IPV4
*Decision: DROP (Drop the connection)
*Protocol: TCP
*SPort (Source Port): 25 (Port used for Email)
*DPort (Destination Port) : None (not specified)
*Source IP: 0.0.0.0/0 (To allow all IP address)
